securing windows with group policy
Josh rickard
@MSAdministrator
Helpdesk
IT System Analyst
System Administrator
Security Analyst
DFIR
Technical Product Manager
Security Research Engineer
Security Solution Architect

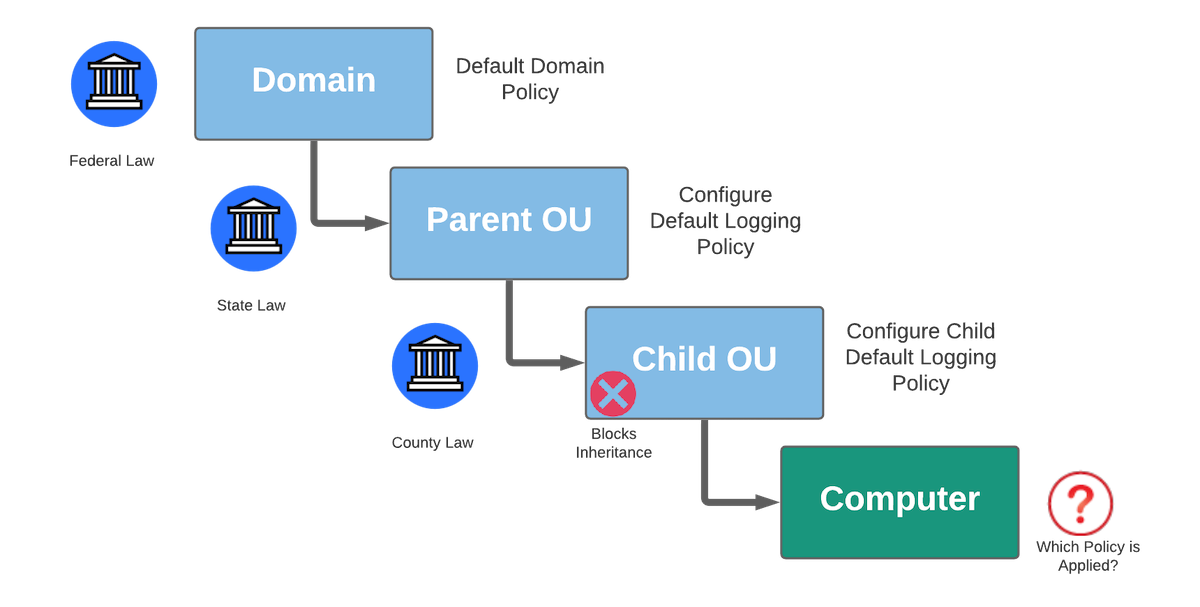
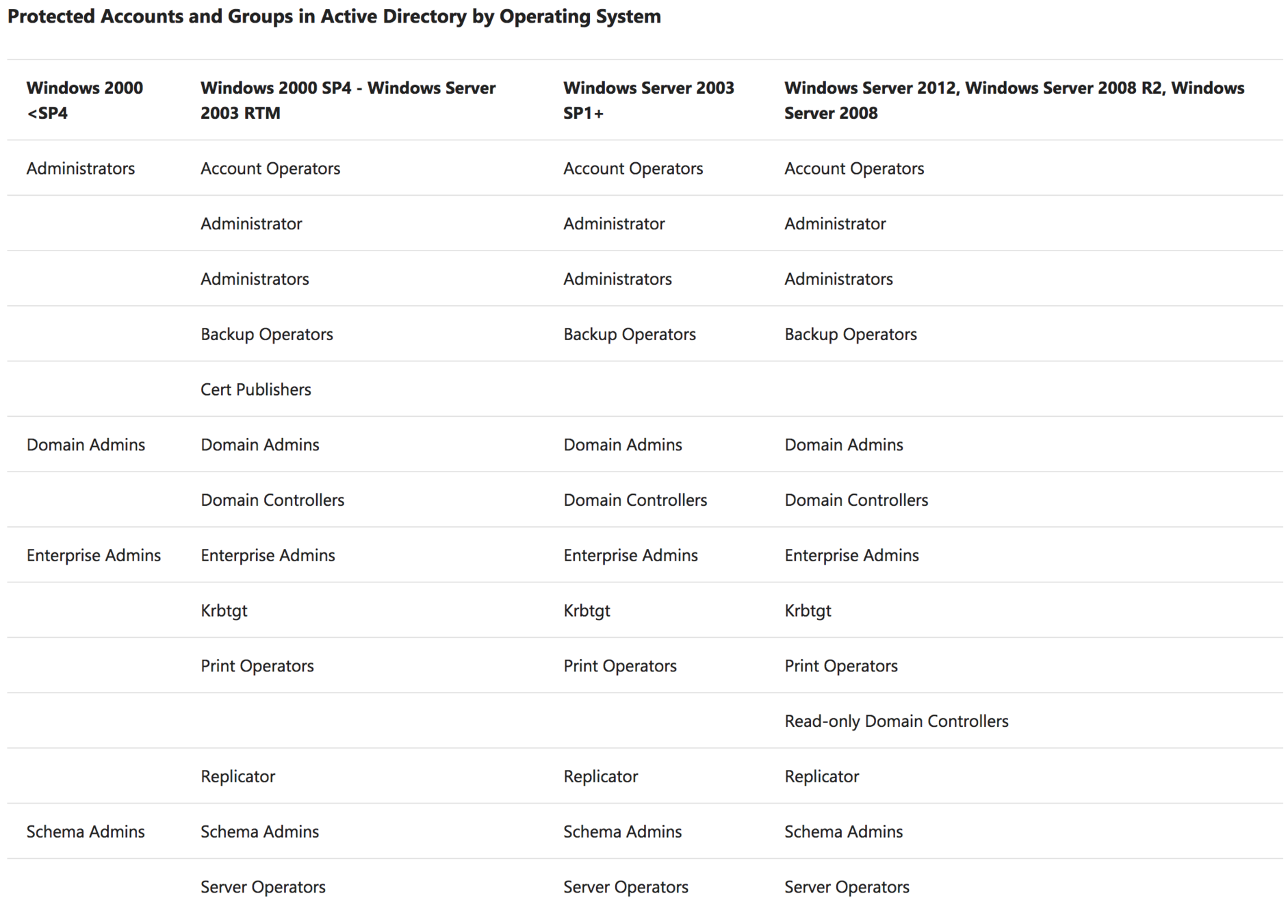
LSD OU
Local

Local group policy
Machine/User specific settings
Free-for-all
Unmanaged
site
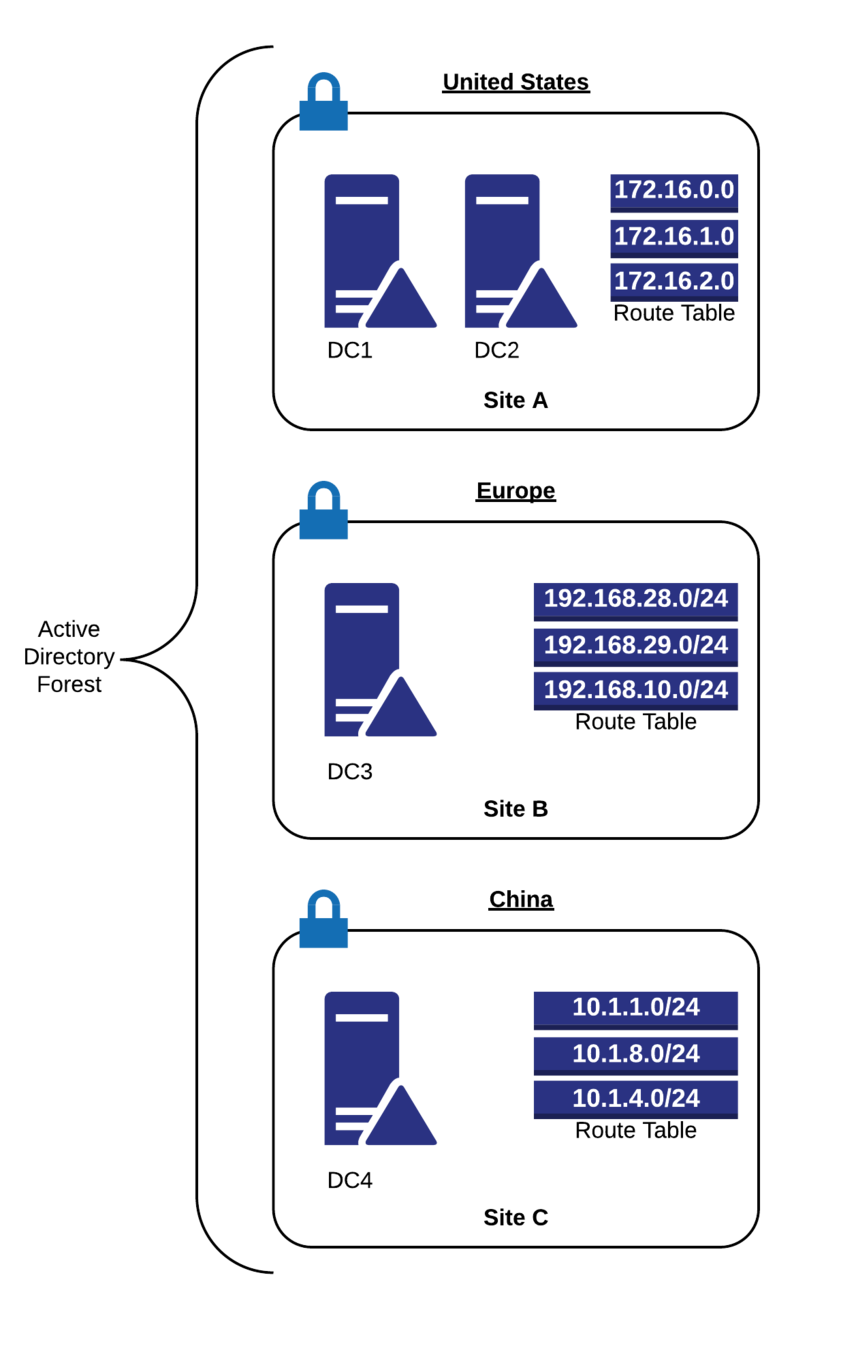
site based group policy
Location based
Subnet based
Forest (or multiple domains)

Domain
Organizational unit
your street

your home

your rooms
Even down to your refrigerator
manage users

Title Text

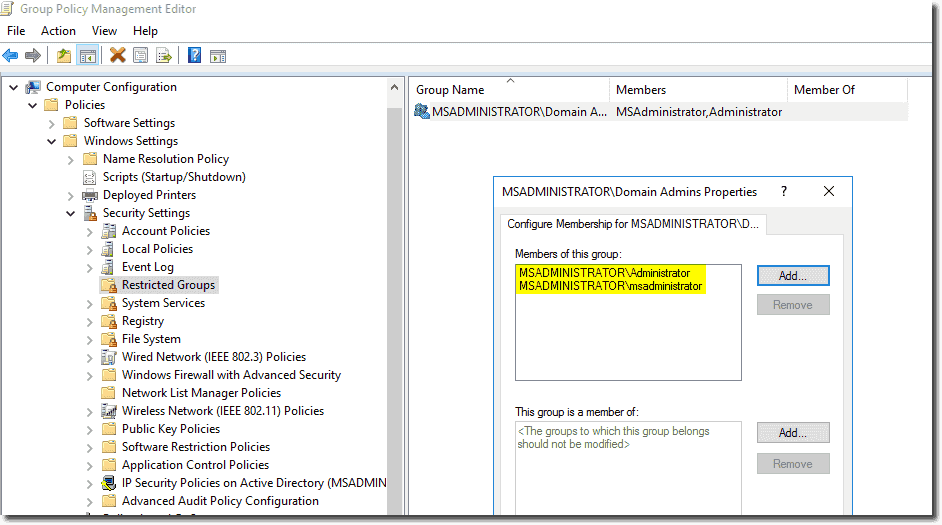
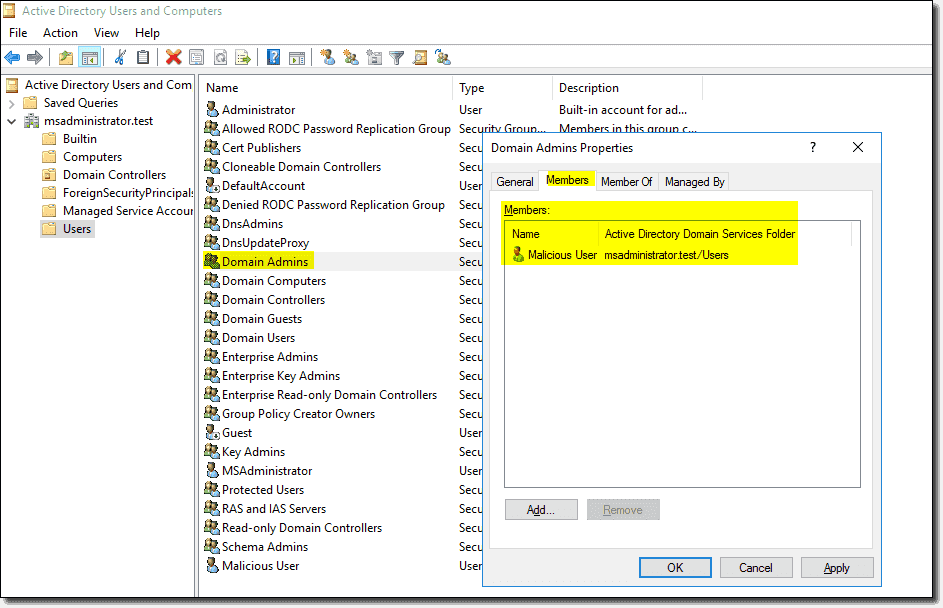
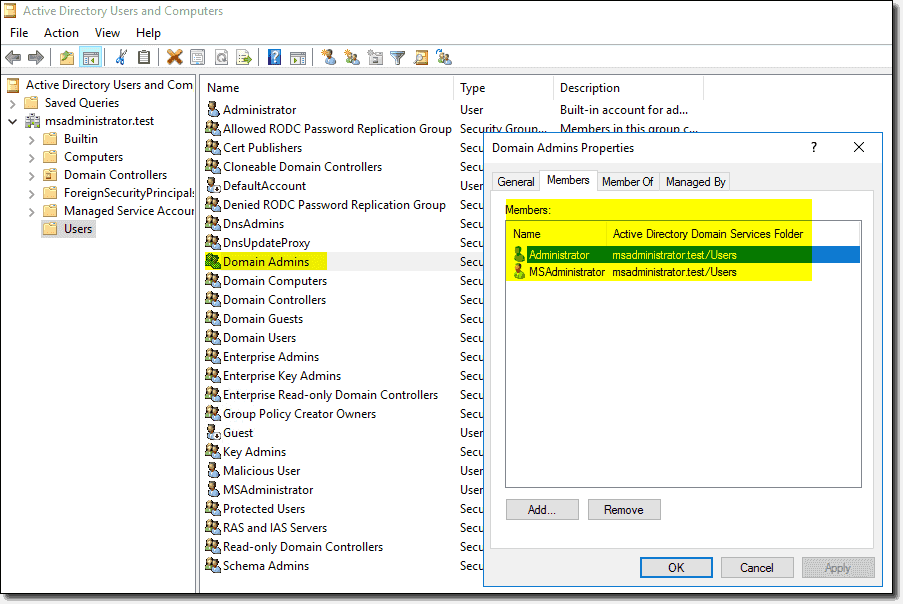
Restricted groups

Title Text
Title Text
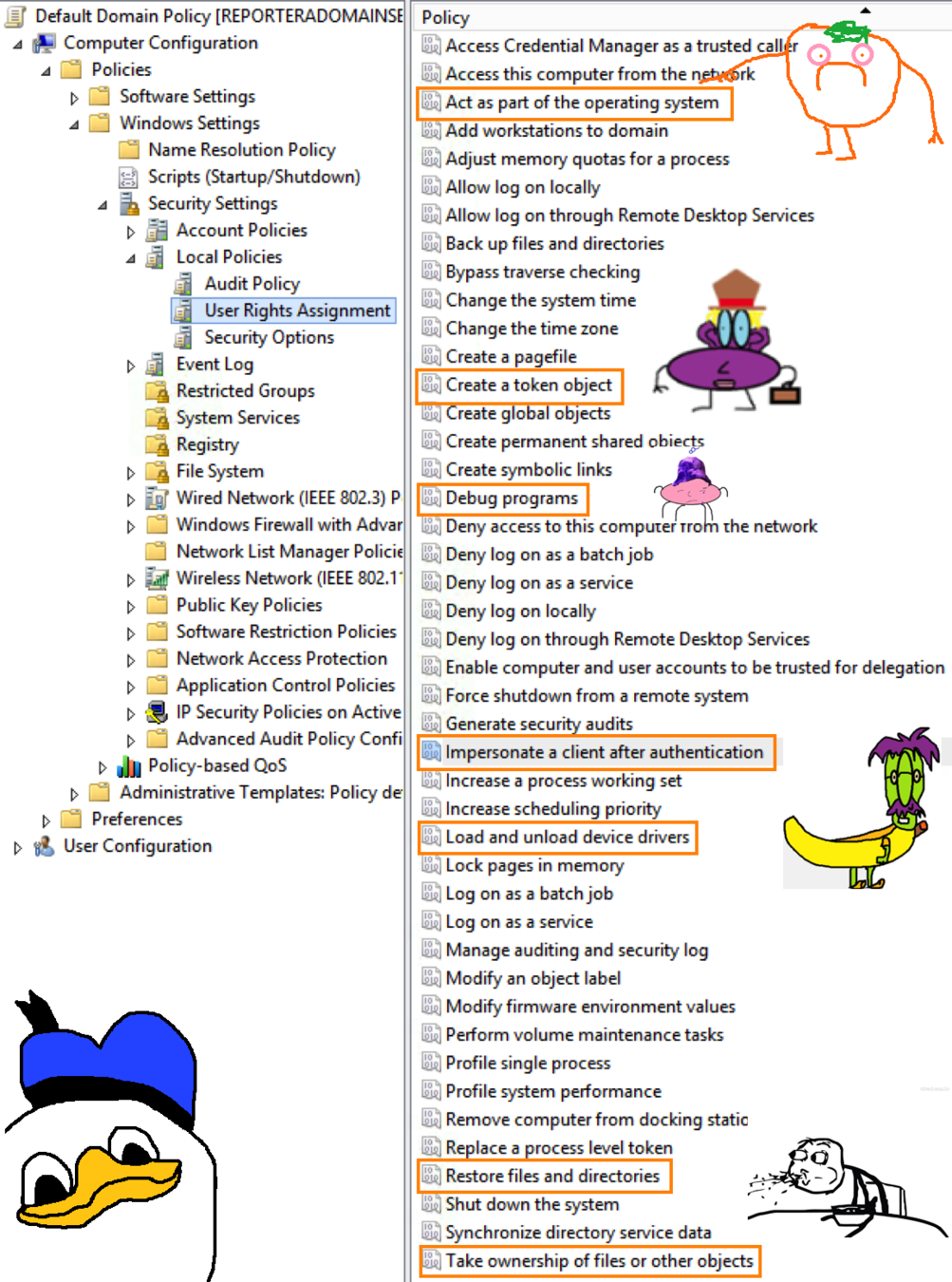
user rights

buying a new home

PRIVILEGES
-
Act As Part of the Operating System
-
Create a Token Object
-
Debug Programs
-
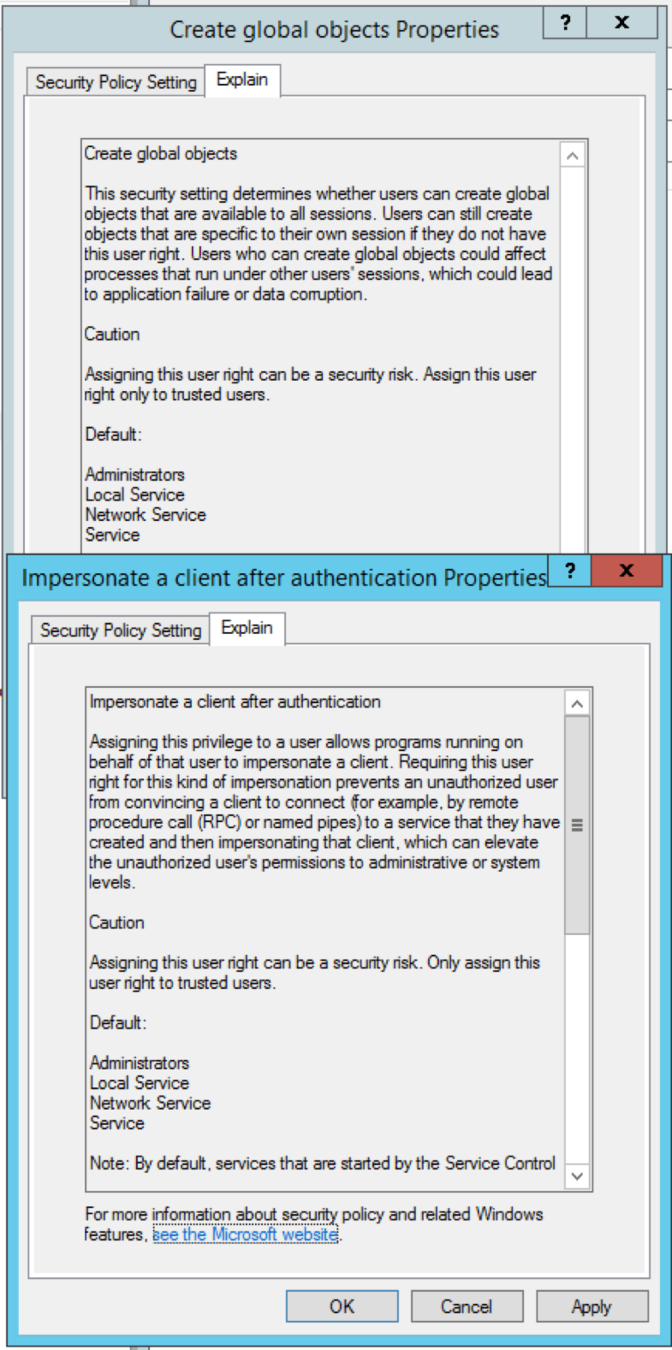
Impersonate a Client After Authentication
-
Load and Unload Device Drivers
-
Restore Files and Directories
-
Take Ownership
Impersonate A Client Privilege
- Primary Security Access Token (SAT)
- Impersonate a user’s SAT for other running processes
- Used by network services to impersonate clients
- Token stealing
- Steal SATs for network authentication
SeImpersonatePrivilege
SeCreateGlobalPrivilege
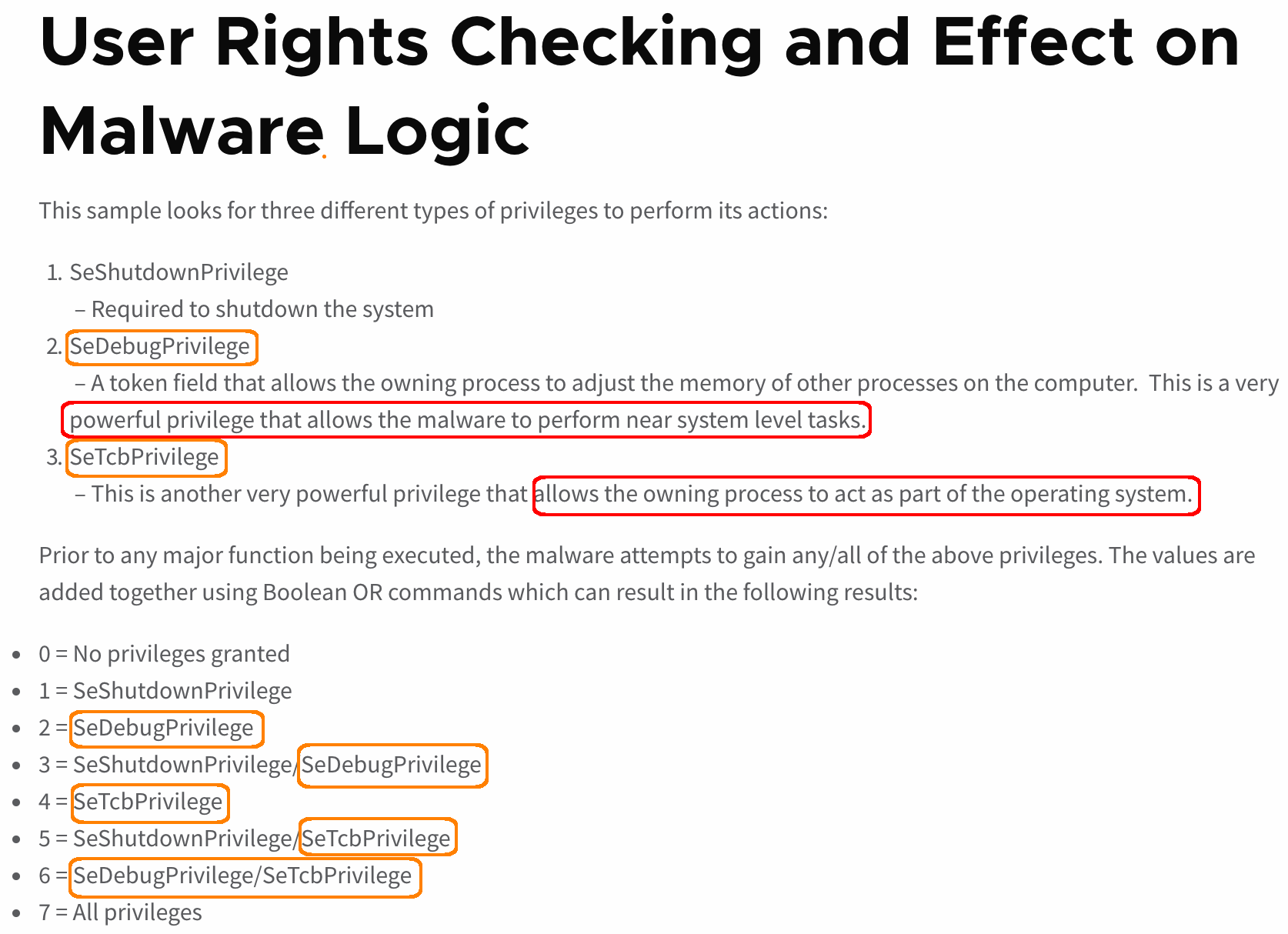
Debug Programs Privilege
-
Grants read/write access to user & kernel-mode memory
-
Malware uses it for:
-
New thread injected into any process
-
Passwords, hashes, encryption keys and other data can be read out of kernel space memory without DLL injection.
-
-
Pass-The-Hash Attacks
-
Once malware has your password hash they can:
-
Extract password hashes of local accounts
-
Extract password hashes of interactive users with AD accounts
-
Plus others
-
-
SeDebugPrivilege
PETyA
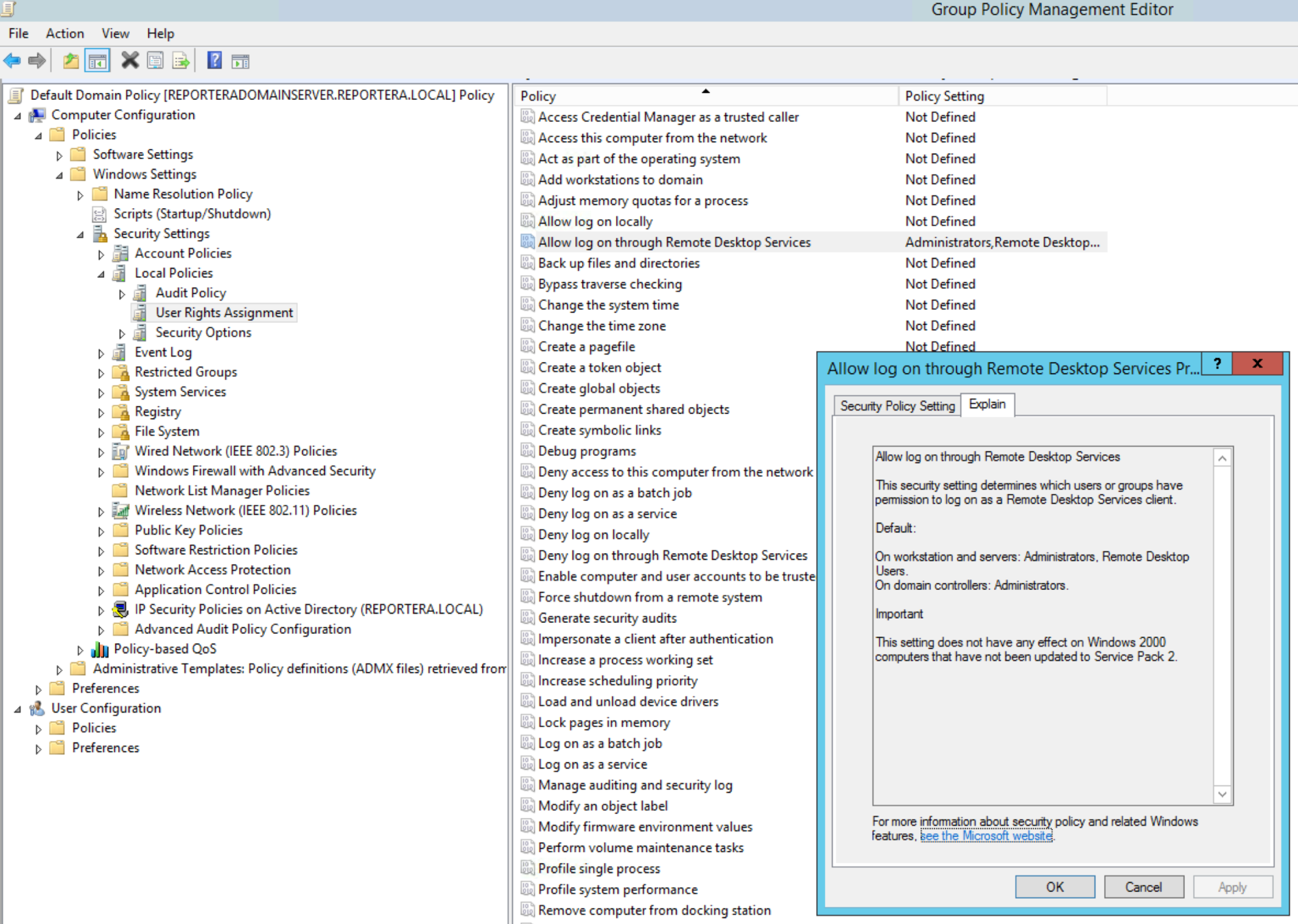
LOgon rights
- Deny access to this computer from the network
- Deny log on as a batch job
- Deny log on locally
- Deny log on as a service
- Deny log on through Remote Desktop Services
- Allow log on through Remote Desktop Services

Title Text
Title Text
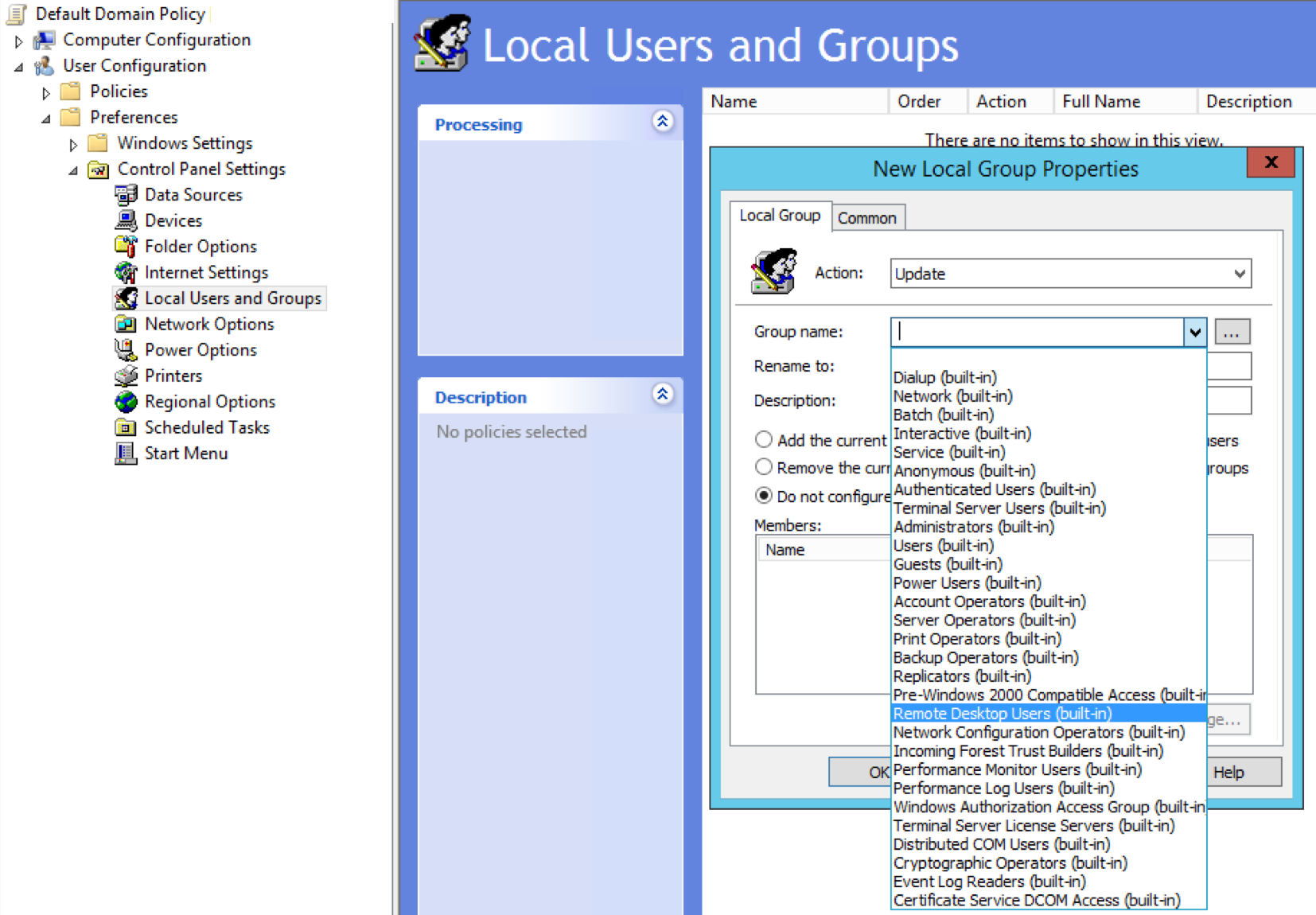
Task scheduler

LEAST to MOST
-
Local Service
-
Virtual Service Account
-
Network Service
-
Local User Account (non-Admin)
-
Group Managed Service Account (domain user)
-
Domain User
-
Local System
-
Local User (local admin)
-
Global User (local admin
-
Global User (domain admin)
-
Global User (Enterprise Admin)
IMMEDIATE SCHEDULED TASKS

-
Program/Script:
- C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
-
Add Arguments:
- -NoProfile -Executionpolicy bypass -file "\\path\to\Invoke-Awesomeness.ps1" -Parameter 'MSPaint'
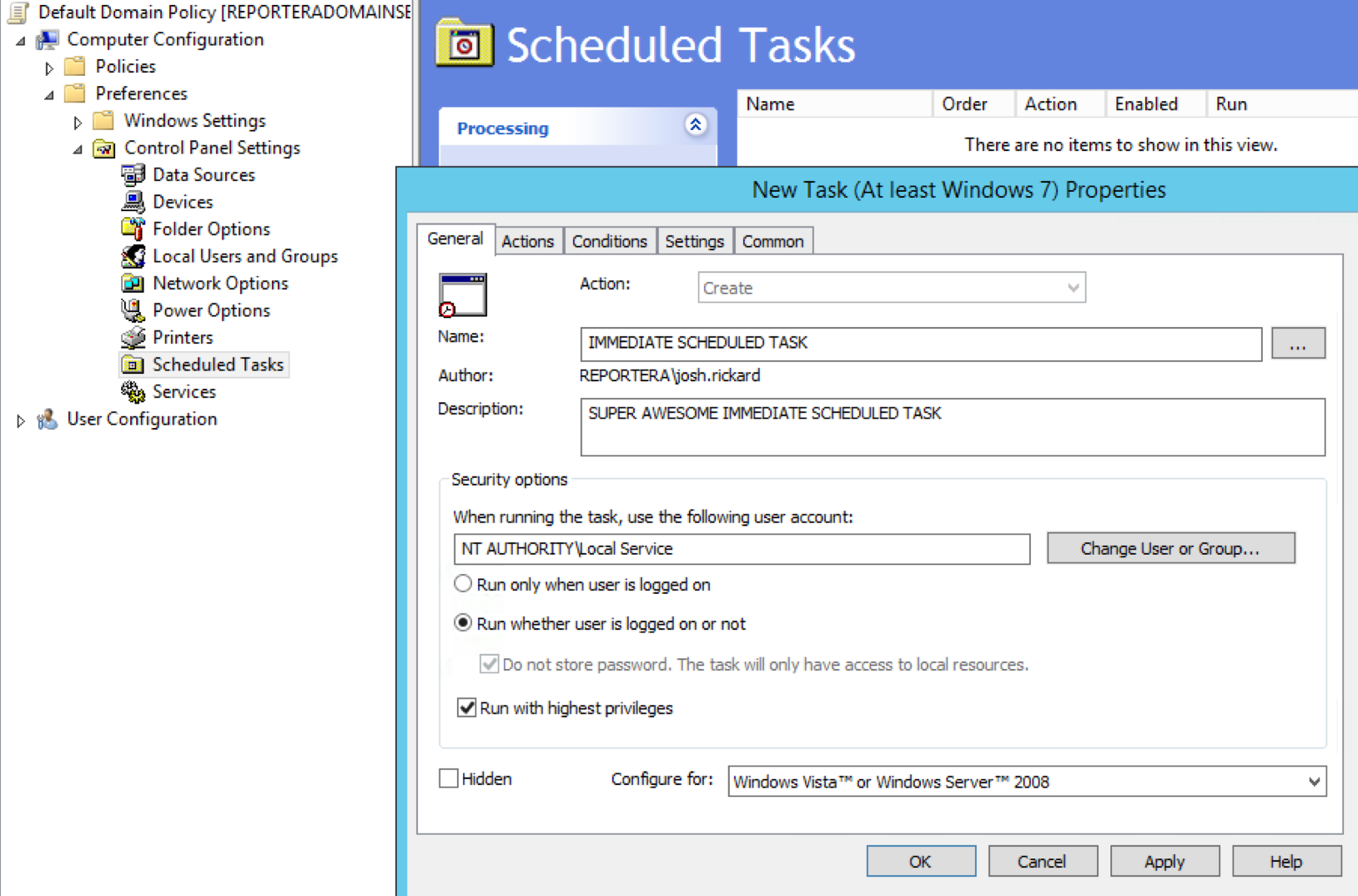
secure code execution
- Run whether user is logged on or not
- Do not store password
- Run with highest privileges

Hint: If you are attempting to communicate over the network, try Network Service first!
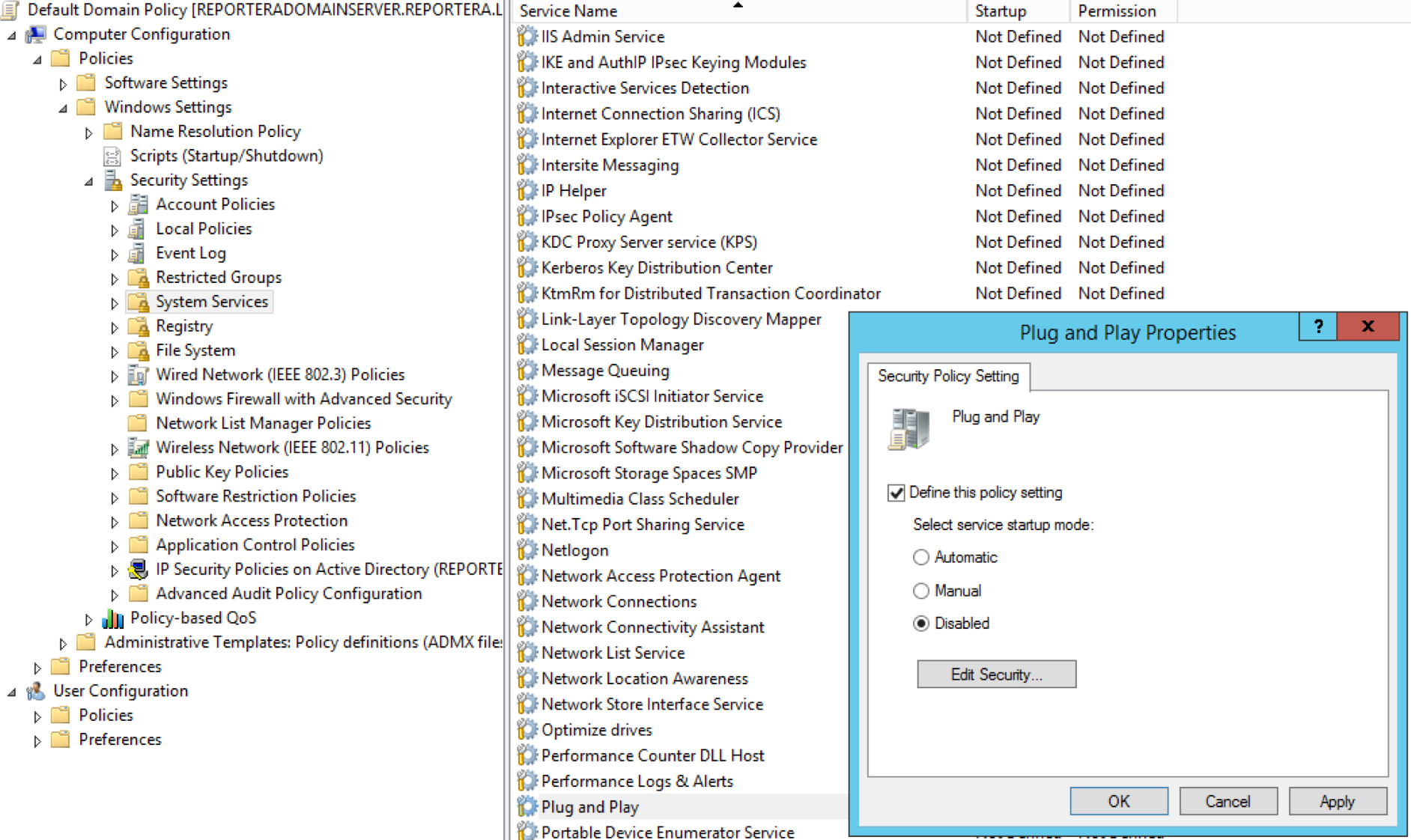
manage services
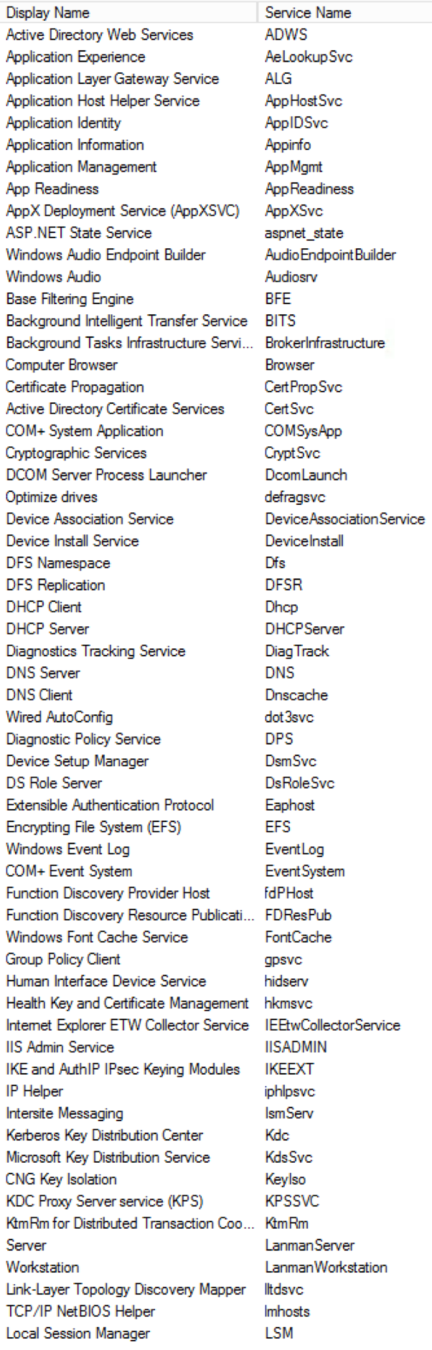
iis server
- DCOM Server Process Launcher
- Event Log
- Protected Storage
- Remote Procedure Call (RPC) Service
- Windows Installer
- Windows NTLM Security Support Provider
- Windows Process Activation Service
- World Wide Web Publishing Service
TURN THEM OFF

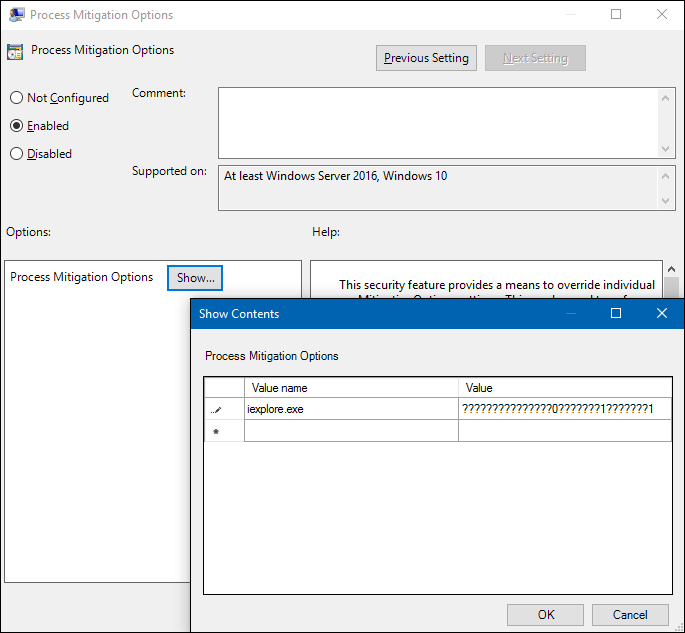
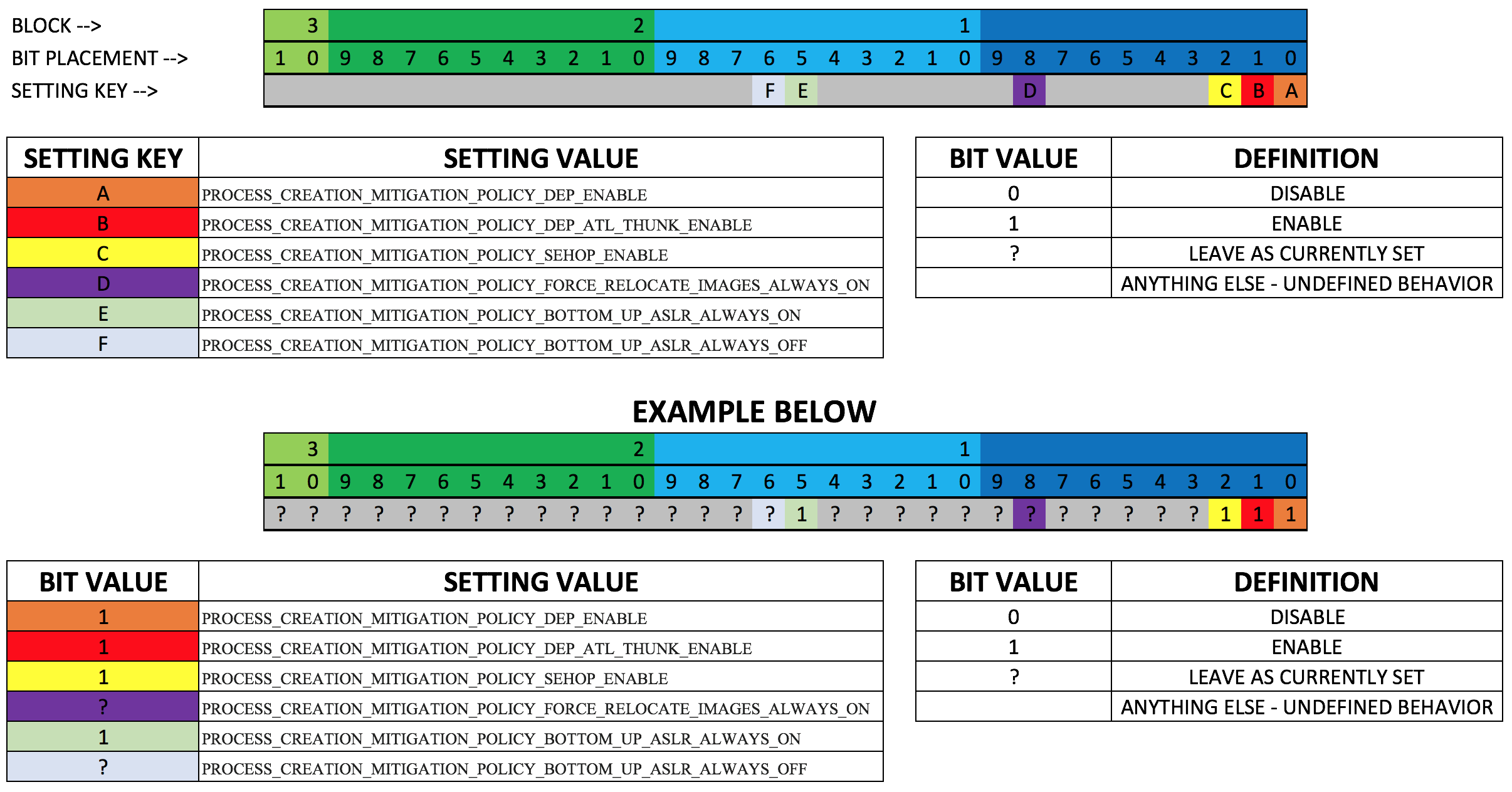
process mitigation



DEP: Data Execution Prevention
SEHOP: Structured Exception Handler Overwrite Protection
ASLR: Address Space Layout Randomization
Text
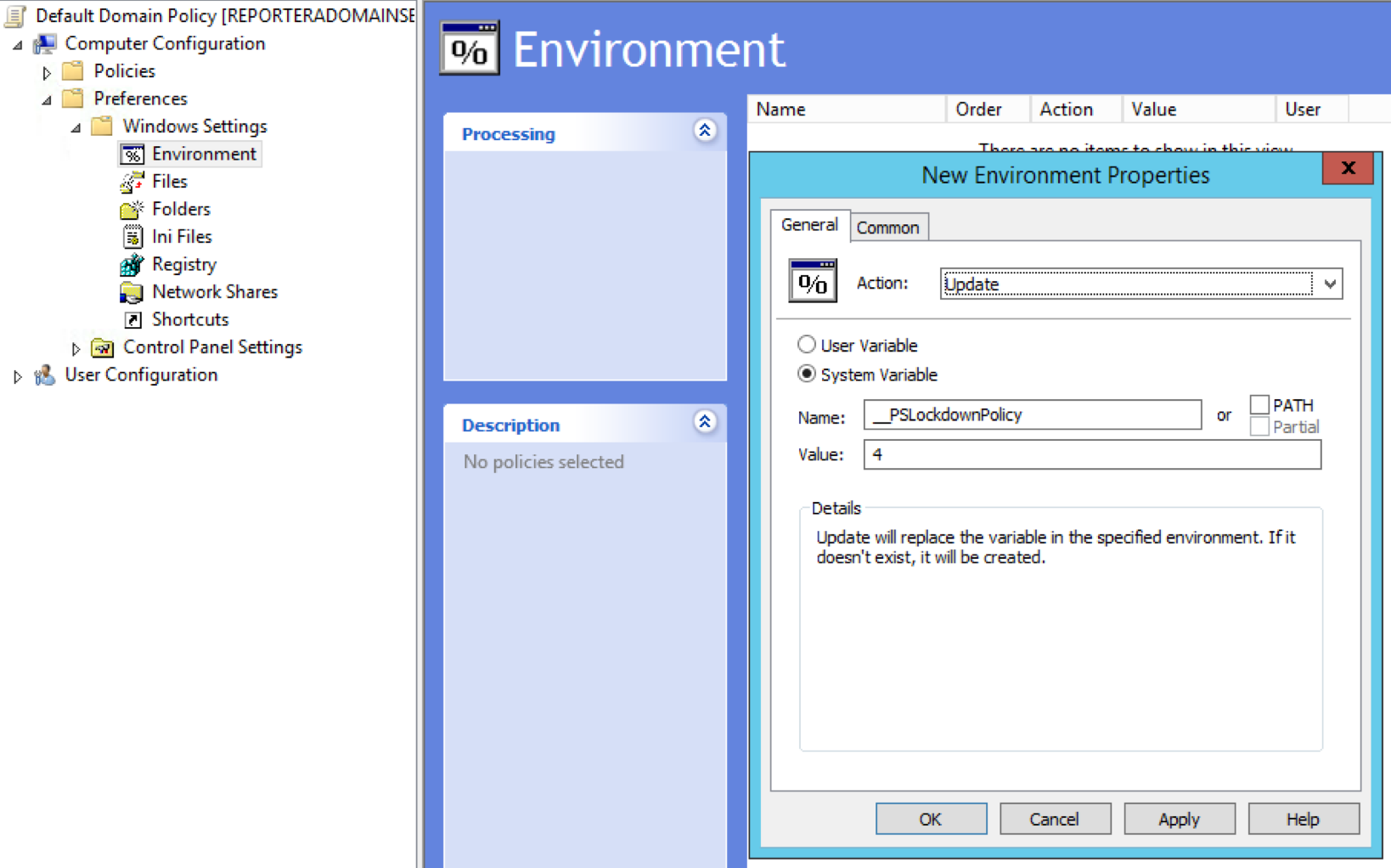
scripting
Powershell
- Enable ALL THE logging
- Lockdown which IPs can use WinRM
- Digitally Sign your scripts
- Use Immediate Scheduled Tasks
IF YOU CAN:
- Use JEA (Just Enough Administration)
- Use AppLocker (ContrainedLanguage Mode)

powershell lockdown policy
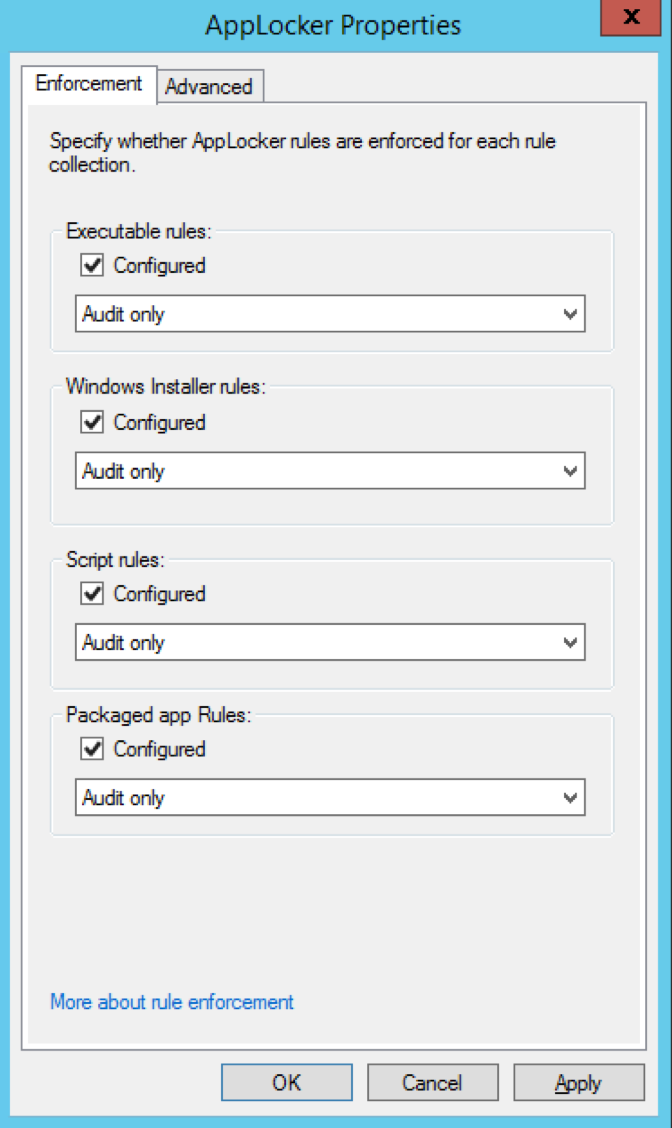
applocker

not so scary
EXEs, DLLs, Scripts, MSIs, APPXs
Three different conditions can be use
- Hash Condition Rules
- Path Condition Rules
- Publisher Condition Rules
BLOCK rules always trump ALLOW rules
HAsh condition
-
Every file has a unique hash value
-
Positive
-
Unique hash for every executable
-
Secure!
-
-
Negative
-
Every update has a new hash
-
PATH CONDITION
- Positive
- Select an entire suite of products
- You can use wildcards (*)
- Negative
- You must know all paths the application uses
- C:\ProgramData
- C:\Users\username\AppData\Local\*\*.zip\*

Publisher condition
- Positive
- Select an entire path to allow a suite of applications
- You can use wildcards (*)
- Negative
- Only works for applications that are digitally signed

https://www.hub.trimarcsecurity.com/post/securing-active-directory-performing-an-active-directory-security-review
thank you

contact
email: rickardja@live.com
blog: https://letsautomate.it
twitter: @MSAdministrator
github: https://github.com/MSAdministrator
slides:
https://letsautomate.it/presentations/securing-windows-with-group-policy.html