Qualysguard Decentralized It How to Organize Your Assets
I work for a University with a decentralized IT department: each college, division, department, etc maintains their users. As a security department who maintains QualysGuard, we were wanting each department to scan their own assets and re-mediate all vulnerabilities found in these scans based on the following policy:
- Level 4 and Level 5 vulnerabilities must be re-mediated within 15 days
- Level 3 vulnerabilities must be re-mediated within 30 days
- Level 2 vulnerabilities must be re-mediated within the next semesters
- Level 1 vulnerabilities must be re-mediated whenever possible
When dealing with QualysGuard in a decentralized IT infrastructure, your naming convention will save you!
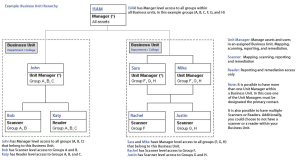
Once you have a group of Assets in their respective Asset Groups, then we add them to their own Business Unit. Remember that you must a Unit Manager (at least 1), and you may any number of Scanner and Reader roles. You can additionally assign a role to specific Asset Groups within the Business Unit (or another Business Unit).
Please see the following graphic, which outlines what was previously stated:
Remember, when you are rolling out your QualysGuard VM infrastructure you will want to plan (in great detail) your roll-out. Creating a roll-out plan that relies on system owners to take responsibility for their own systems, instead of System Administrators and/or Security Analyst is the idea goal. By doing this, it highlights the importance for security in your organization as well as giving everyone insight into the security posture of their organization. Hopefully they will see QualysGuard as a tool of transparency that helps strengthen your organization vulnerability management life cycle management.